Cyber Security Enthusiast | OSCP | CEH | CHFI | CNSS | Master of IT Security & Master of IT Management
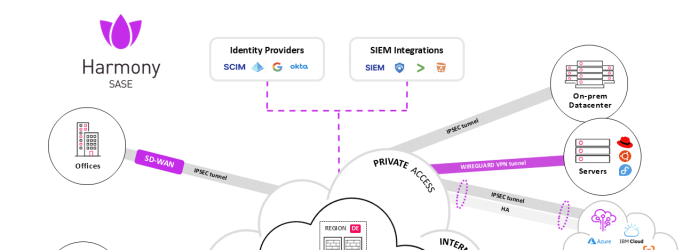
As organizations embrace cloud computing, remote work, SaaS applications, and distributed teams, traditional perimeter-based security models are no longer effective. Backhauling traffic through a central data center introduces latency,...
Below is the cheatsheet for network admins for subnet masks: / Addresses Hosts Netmask Amount of a Class C...
There are several commands and things you can’t do if you have a non-tty-shell. This can occur if you...
Before diving into the differences between these two, we need to understand that what penetration testing (aka pen-testing) is....
This is for pure educational & informational purpose. Only use these techniques where allowed or you have permission to...
A buffer overflow condition exists when a program attempts to put more data in a buffer than it can...
