- Skip to primary navigation
- Skip to main content
- Skip to primary sidebar
- Skip to footer
- Skip to footer navigation
e-mail: info@catharsis.net.au | Telephone: 1300 342 276
Australia's Leading Cybersecurity Company
Catharsis is a certified ISO 27001:2022 compliant company
Cybersecurity Simplified
Our goal is to offer a simplified approach to Cybersecurity, giving customers comfort that their exposure to the threat of becoming a victim to a cyber incident is dramatically reduced. According to the IBM Cyber Security Intelligence Index Report, 95% of cybersecurity breaches are caused by some form of human error. An incredible 91% of cyber-attacks begin with a phishing email to an unsuspecting victim. In the 2023 State of Email Security Survey, 97% of organizations claim to have been targeted by phishing attacks.
With this in mind, our approach begins by recognizing the importance of the human factor and developing solutions that solve these issues by focusing on the critical areas known for posing the greatest risk;
Endpoint security refers to the cybersecurity strategy employed to safeguard endpoints, including desktops, laptops, and mobile devices, from malicious activities and threats. Endpoint security is a cornerstone to cyber security and comes in many shapes and sizes. We help by offering simple and affordable solutions that can grow with you.
Given its position as the number 1 attack vector, email protection is essential to safeguard your organisation against sophisticated, multi-stage attacks. We configure tools to proactively keep ahead of evolving threats and minimise the chance of human error playing a part in you becoming a victim to a cyber-attack.
Vulnerability management involves a continuous and systematic approach to identifying, evaluating, reporting, managing, and remediating cyber vulnerabilities present in your applications and network. We take a risk-based prioritisation approach allowing for a logical order in which to tackle your to-do list, keeping risk exposure at an all time low.
With human error being the most likely point of initiation of a cyber-attack it makes sense that cybersecurity awareness should be a focus. Using a combination of minutes long, bite sized training sessions along with phishing simulations, all designed to drive changes in behaviour, we ensure that awareness remains front of mind and human error is dramatically reduced.
The Three Pillars to Success
While we take a Human Centric approach, establishing an effective and robust cybersecurity stance necessitates a system founded on three fundamental pillars. People, Processes and Technology.
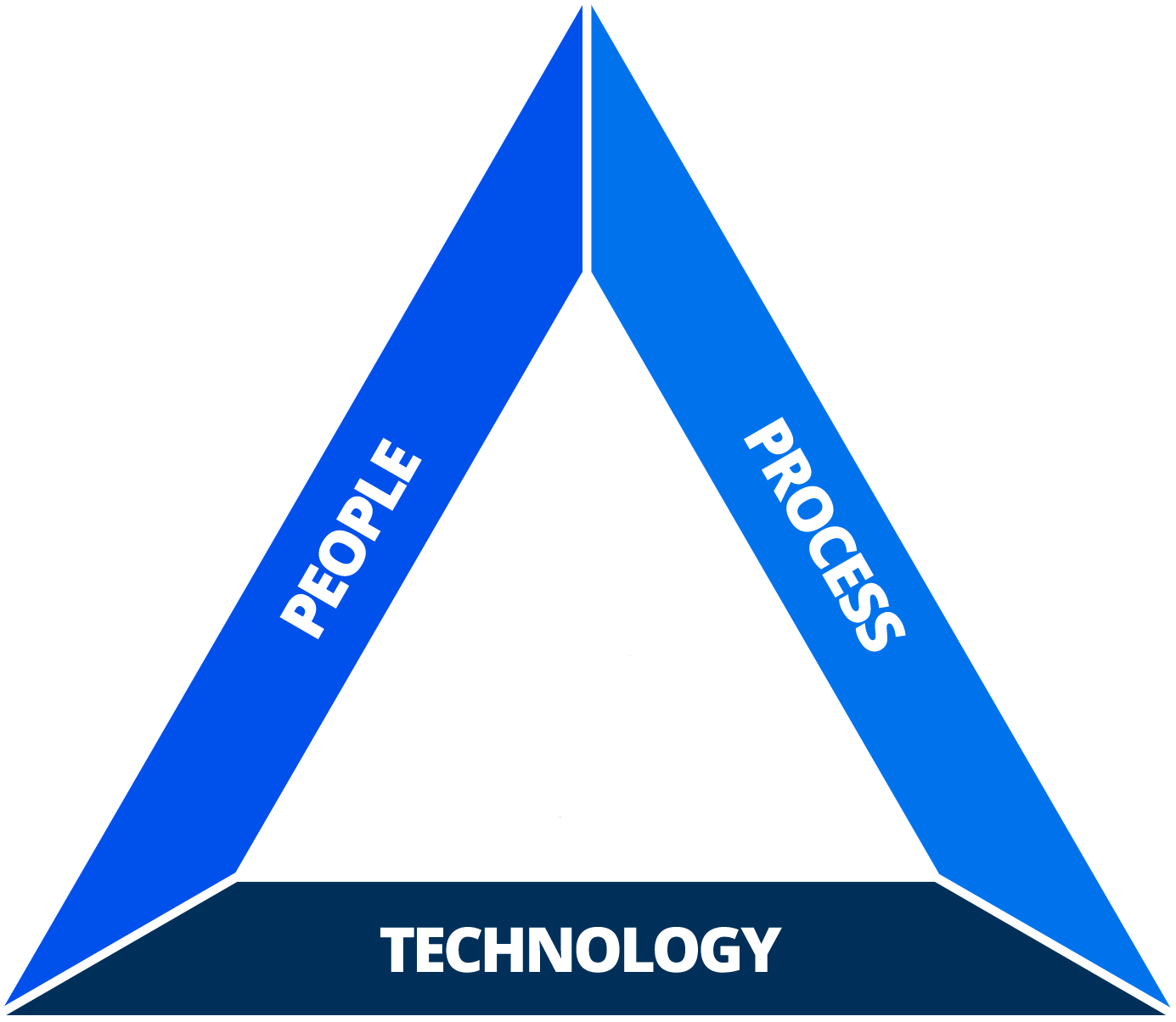
People: The Human Factor upon which we structure our approach. People are your biggest risk, but also offer you the opportunity to drive your greatest shift in security posture by honing their skills to minimise your risk.
Process: The way in which you manage your internal policy and procedural driven approach to how people use all of the technological elements of your business that expose you to risk.
Technology: This is what we build around the people to drive improved behaviour, reduced risk and promote ongoing awareness.
Each pillar is as important as the next. We cannot shift the balance on one without tweaking the balance on the remaining two.
With our Human Centric approach, we cover the People and Technology components of the Three Pillars by default. We incorporate Process using the Australian Cyber Security Centre's (ACSC) Essential 8 Framework.
The ACSC Essential 8 Framework is a comprehensive cybersecurity guideline developed by the Australian Cyber Security Centre (ACSC) to help organisations strengthen their defense against cyber threats. It provides a strategic framework consisting of eight key mitigation strategies that organisations should prioritise and implement to improve their overall cybersecurity posture.
The Essential 8 Framework encompasses a range of proactive and reactive security controls that focus on key areas of cyber security. They include:
/* CSS styles for list items */ .list-container p { margin-bottom: 5px; /* Adjust the spacing between list items */ } /* CSS styles for the list container */ .list-container { margin-bottom: 25px; /* Adjust the spacing before the new paragraph */ }
1. Application Whitelisting
2. Patching Applications
3. Configuring Microsoft Office Macro Settings
4. User Application Hardening
5. Restricting Administrative Privileges
6. Patching Operating Systems
7. Multi-Factor Authentication (MFA)
8. Daily Backups
The Australian Signals Directorate have stated that implementing the Top 4 mitigation strategies can assist in preventing over 85% of unauthorised intrusions.
Cyber Security Partnerships across
10+ Major Industries
partners & technology
We partner with industry-leading solutions providers and vendors to ensure that we provide you with the best and most up-to-date security controls.








Top FAQs for Catharsis
We offer a wide range of cyber security services, including risk assessment and management, managed security services, Email Protection, Security Awareness Training, advanced threat protection, data protection and privacy, cloud security solutions and more.
We adhere to strict data privacy regulations and help businesses comply with relevant laws and standards. Our strategies involve regular audits, compliance checks, and implementing the latest data protection protocols.
Absolutely. We specialize in advanced threat protection, employing proactive measures to safeguard against ransomware and other sophisticated cyber threats. Our approach involves both preventing attacks and rapidly responding to any incidents.
Yes, we recognize that different industries face unique cybersecurity challenges. Our Certified team specializes in creating customized solutions that cater to the specific needs and regulations of various sectors.
Our incident response protocol is swift and efficient, involving immediate identification of the threat, containment of the breach, eradication of the threat, and recovery processes. Our Expert team also conduct post incident web security analysis to prevent future occurrences.
We stay ahead by continuously updating our knowledge and tools, attending industry conferences, and engaging in ongoing training. Our expert team closely monitors the cybersecurity landscape to anticipate and prepare for emerging threats.
The first step is a comprehensive cybersecurity assessment conducted by our experts. This evaluation helps us understand your current security posture and identify areas for improvement.
Effectiveness is measured through regular security audits, penetration testing, and monitoring key performance indicators related to cybersecurity. Client feedback and incident response outcomes also play a significant role.
Cybersecurity Consulting
Our team of strategic and technical subject matter experts comprehensively grasp your cybersecurity requirements. We offer cybersecurity services that encompass assessment, development, implementation, and management of tailored, next-generation solutions to address your specific needs.
Penetration Testing
Penetration testing is an important part of any cybersecurity program. By conducting pen tests, organisations can identify weaknesses in their security posture and take proactive steps to address them, reducing the risk of data breaches, financial losses, and reputational damage.
Incident Response Planning
It is crucial to have a cyber incident response plan to ensure an effective response and prompt recovery in the event security controls don’t prevent an incident occurring. The plan should outline the steps used to prepare for, detect, contain, and recover from a data breach.
Cloud Security
Use cloud security to assess all assets within your cloud infrastructure so you can discover, mitigate and remediate all vulnerabilities, weaknesses and misconfigurations to keep your cloud infrastructure safe.
Managed Firewall Service
Allow our experts to review, design, implement, monitor, and maintain firewalls to control the flow of traffic across your networks and prevent unauthorised access, malware infections, and other cyber threats.
Network Monitoring
Effective network monitoring requires the use of specialised tools which capture and analyse network and WAN traffic in real-time, allowing us to quickly identify and respond to security threats and other issues.

Web Development
Our web development services cater to customers of all types and sizes. Whether you’re an entrepreneur looking to build or upgrade your e-commerce website, a not-for-profit organisation wanting to refresh your web presence and add functionality or a global accounting firm looking to streamline your web processes, we can develop a customised solution tailored to the specific needs of your business.
SEO & Digital Marketing
SEO is a critical element of any digital marketing strategy. While it requires time and ongoing effort, the results are always worth the effort and offer excellent long-term benefits. In a world where new websites are popping up every day, staying relevant, updated and useful is essential. Let us help identify and implement the right SEO strategy for your business and weave it into your broader Digital Marketing strategy to drive ongoing success.

O365 G-Suite Migration
Need to migrate data and applications from Microsoft’s Office 365 (O365) platform to Google’s G Suite. Let us help. The Office 365 to G-Suite migration process can be complex and time-consuming, requiring specialised skills and expertise in both O365 and G Suite platforms, as well as data migration tools and technologies. This migration typically involves transferring emails, contacts, calendars, files, and other data between the two platforms, while ensuring data integrity, security, and availability.

Sign Up Now for Newsletter
Want to stay up-to-date with on-going security threats?
- walk-through & POC's
- Latest bugs & Vulnerabilties
- new innovations & services by Catharsis
Footer

An ACSC Partner
Connect with Us
Fibaro Pty Ltd
Address: 49 28 Barcoo Street, Roseville NSW(2069)
Phone: 1300 342 276 | Email: info@catharsis.net.au
