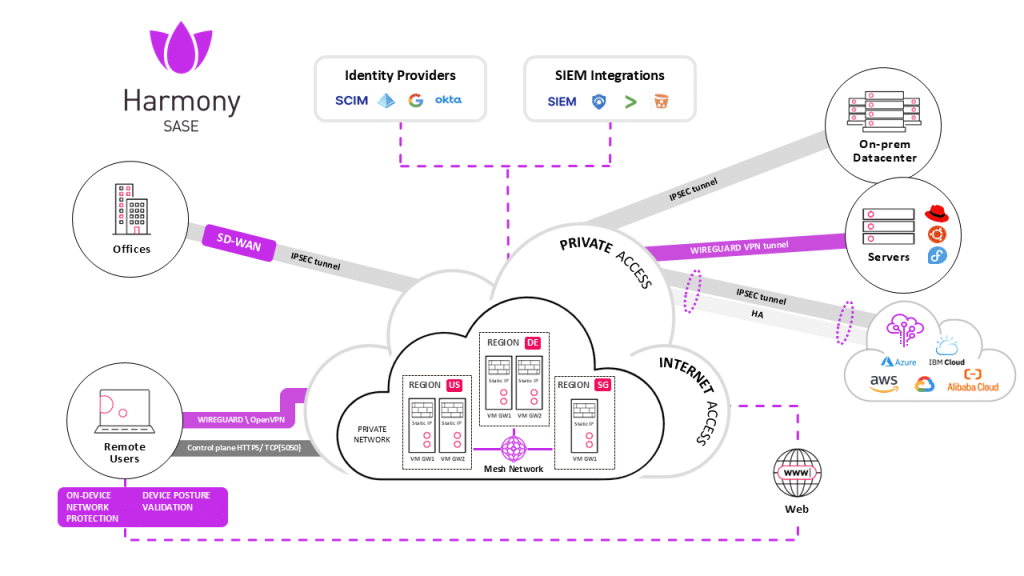
As organizations embrace cloud computing, remote work, SaaS applications, and distributed teams, traditional perimeter-based security models are no longer effective. Backhauling traffic through a central data center introduces latency, complexity, and risk.
This is where Secure Access Service Edge (SASE) becomes essential.
In this guide, we’ll break down:
What SASE is
Core components and terminology
How it differs from traditional security models
Benefits and challenges
Implementation strategy
Why SASE is critical for modern Australian businesses
What is Secure Access Service Edge (SASE)?
Secure Access Service Edge (SASE) is a cloud-delivered architecture that converges networking and security services into a unified platform.
The term was introduced by Gartner in 2019. According to Gartner, SASE combines:
- WAN capabilities
- Comprehensive network security functions
- Delivered as a cloud-native service
- Based on identity-driven policies
- Globally distributed via points of presence (PoPs)
In simple terms:
SASE brings networking and security together into one cloud-based service that securely connects users, devices, and applications — anywhere.
Why Traditional Security Models No Longer Work
Historically, organizations used:
- MPLS networks
- Centralized data centers
- Hardware firewalls
- VPN concentrators
- Castle-and-moat security models
This approach assumed:
- Users worked in offices
- Applications lived in data centers
- Security perimeter was fixed
Today’s reality:
- Applications are in Microsoft 365, AWS, Azure, and SaaS platforms
- Employees work remotely
- Contractors require controlled access
- Devices connect from anywhere
Backhauling traffic through a central firewall:
- Increases latency
- Creates bottlenecks
- Expands attack surfaces
- Raises operational costs
SASE eliminates these limitations.
Core Components of SASE
SASE is not a single product. It is an architectural model composed of several technologies.
1. SD-WAN (Software-Defined Wide Area Network)
SD-WAN replaces traditional MPLS networks by:
- Using multiple internet links
- Intelligently routing traffic
- Optimizing application performance
- Reducing WAN costs
It provides:
- Application-aware routing
- Centralized management
- Resilient connectivity
SD-WAN handles the networking side of SASE.
2. Secure Web Gateway (SWG)
A Secure Web Gateway protects users from web-based threats.
Key capabilities:
- URL filtering
- Malware protection
- Content inspection
- HTTPS decryption
- Acceptable use policy enforcement
SWG ensures safe internet access.
3. Cloud Access Security Broker (CASB)
CASB provides visibility and control over SaaS applications.
Functions include:
- Shadow IT discovery
- Data Loss Prevention (DLP)
- Threat detection in SaaS
- Compliance enforcement
- API-based cloud monitoring
It protects data in cloud applications.
4. Firewall as a Service (FWaaS)
FWaaS delivers next-generation firewall capabilities from the cloud:
- Intrusion Prevention (IPS)
- Deep Packet Inspection
- Application control
- Threat intelligence
- SSL inspection
Unlike traditional firewalls, FWaaS scales globally.
5. Zero Trust Network Access (ZTNA)
ZTNA replaces traditional VPNs.
Core principles:
- Never trust, always verify
- Identity-based access
- Least-privilege access
- Continuous authentication
Users only access specific applications — not entire networks.
This reduces lateral movement risks.
Key SASE Terminologies Explained
Understanding SASE requires familiarity with several key terms.
Zero Trust
A security model where no user or device is trusted by default, regardless of location.
PoP (Point of Presence)
Global cloud locations where SASE services are delivered to users for low latency.
SSE (Security Service Edge)
A subset of SASE focused purely on security (SWG, CASB, FWaaS, ZTNA) without SD-WAN.
Identity-Centric Security
Access policies based on:
- User identity
- Device posture
- Location
- Risk score
Edge Computing
Processing and enforcing policies closer to the user instead of a central data center.
Benefits of Implementing SASE
1. Enhanced Security Posture
- Reduced attack surface
- Zero Trust enforcement
- Centralized visibility
- Consistent policy enforcement
2. Improved Performance
- Direct-to-cloud access
- Reduced backhaul latency
- Intelligent traffic routing
3. Reduced Operational Complexity
- Consolidated vendors
- Single management console
- Cloud-delivered updates
4. Lower Infrastructure Costs
- Reduced MPLS dependency
- Fewer hardware appliances
- Simplified branch deployment
5. Better Support for Remote Work
Ideal for:
- Hybrid teams
- Field workers
- Contractors
- Global offices
SASE vs Traditional Network Security
| Feature | Traditional Model | SASE Model |
|---|---|---|
| Security Location | Data Center | Cloud |
| Remote Access | VPN | ZTNA |
| WAN | MPLS | SD-WAN |
| Scalability | Hardware Dependent | Cloud Elastic |
| Policy Control | Location-Based | Identity-Based |
SASE vs SSE: What’s the Difference?
SASE = Networking + Security
SSE = Security Only
SSE includes:
- SWG
- CASB
- FWaaS
- ZTNA
But does not include SD-WAN.
Organizations may adopt SSE first, then evolve into full SASE.
Challenges in SASE Adoption
While powerful, SASE implementation requires:
- Architectural redesign
- Identity management maturity
- Cloud readiness
- Policy consolidation
- Vendor evaluation strategy
Common challenges:
- Integrating legacy systems
- Migration from VPN
- Managing SSL decryption at scale
- Ensuring global PoP coverage
How to Implement SASE Successfully
Step 1: Assess Current Architecture
- Network topology
- Security stack
- User distribution
- Application hosting
Step 2: Define Zero Trust Strategy
- Identity provider integration
- MFA enforcement
- Device posture checks
Step 3: Consolidate Security Policies
- Standardize access controls
- Define data protection rules
- Remove redundant firewall rules
Step 4: Choose the Right Vendor
Evaluate:
- Global PoP presence
- Performance SLAs
- Integration capabilities
- API support
- Reporting and visibility
Step 5: Phased Migration
- Pilot with remote users
- Replace VPN with ZTNA
- Gradually migrate branch connectivity
Why SASE Matters for Australian Businesses
For Australian organizations:
- Remote workforce across cities
- Increasing ransomware attacks
- Cloud-first strategies
- Compliance obligations (e.g., Essential Eight)
- Rising cyber insurance requirements
SASE enables:
- Centralized control across distributed teams
- Stronger identity-based access
- Scalable security without heavy hardware investments
For MSP and MSSP providers like Catharsis, SASE offers an opportunity to:
- Deliver managed cloud security
- Provide Zero Trust architecture
- Improve client visibility
- Reduce operational complexity
The Future of SASE
SASE continues to evolve with:
- AI-driven threat detection
- Secure IoT integration
- Browser isolation
- Data-centric security
- Continuous risk-based authentication
As digital transformation accelerates, SASE is becoming the foundation of secure networking.
Final Thoughts
Secure Access Service Edge (SASE) is not just another cybersecurity buzzword — it represents a fundamental shift in how organizations design networks and enforce security.
By converging:
- SD-WAN
- ZTNA
- SWG
- CASB
- FWaaS
Into a unified cloud-native architecture, SASE delivers:
- Better security
- Better performance
- Better scalability
- Better user experience
Organizations that embrace SASE position themselves for a secure, scalable, cloud-first future.
If you’re planning to modernize your network security architecture or explore a Zero Trust strategy, evaluating a SASE framework is no longer optional — it’s strategic.